Meltdown and Spectre Vulnerability
Meltdown (CVE-2017-5754) and Spectre (CVE-2017-5753 and CVE-2017-5715) are the names of the two security vulnerabilities found in processors from Intel, ARM and AMD. Both these vulnerabilities make use of ‘speculative execution’ through which a less privileged user process can access privileged memory which are restricted to be used only by kernel thereby allowing attackers to read secrets of other programs and operating system.
To understand what ‘speculative execution’ is and how these vulnerabilities work, you can refer the below links.
-
- Xen project
There are whole lot of applications, devices and servers affected because of this that includes – Windows OS, Edge/IE – Apple macOS, iOS, tvOS – Android OS – Firefox – Chrome etc. Fixes for most of these are already available and it is advised to do an update to apply those fixes. You can refer this blog to get the list of updates available for various applications and versions.
This article focuses only on identifying and addressing this vulnerability in linux servers. There have been speculations stating the workaround/patching can degrade the performance of the server. The steps described below are just suggestions and its upto the readers to do a research before implementing it in their environment.
How to identify if your Linux server is affected ?
There is already a shell script (Spectre & Meltdown Checker) available that identifies if your server is vulnerable or not. The script will check if your Linux installation is vulnerable against the 3 “speculative execution” CVEs.
CVE-2017-5753 bounds check bypass (Spectre Variant 1)
- Impact: Kernel & all software
- Mitigation: recompile software and kernel with a modified compiler that introduces the LFENCE opcode at the proper positions in the resulting code
- Performance impact of the mitigation: negligible
CVE-2017-5715 branch target injection (Spectre Variant 2)
- Impact: Kernel
- Mitigation 1: new opcode via microcode update that should be used by up to date compilers to protect the BTB (by flushing indirect branch predictors)
- Mitigation 2: introducing “retpoline” into compilers, and recompile software/OS with it
- Performance impact of the mitigation: high for mitigation 1, medium for mitigation 2, depending on your CPU
CVE-2017-5754 rogue data cache load (Meltdown)
- Impact: Kernel
- Mitigation: updated kernel (with PTI/KPTI patches), updating the kernel is enough
- Performance impact of the mitigation: low to medium
Clone the Spectre & Meltdown Checker script from github
$ git clone https://github.com/speed47/spectre-meltdown-checker
Cloning into 'spectre-meltdown-checker'...
remote: Counting objects: 209, done.
remote: Compressing objects: 100% (5/5), done.
remote: Total 209 (delta 2), reused 7 (delta 2), pack-reused 202
Receiving objects: 100% (209/209), 72.38 KiB | 0 bytes/s, done.
Resolving deltas: 100% (119/119), done.
Checking connectivity... done.
The script without options will inspect you currently running kernel. You can also specify a kernel image on the command line, if you’d like to inspect a kernel you’re not running. The script should be executed as sudo or root.
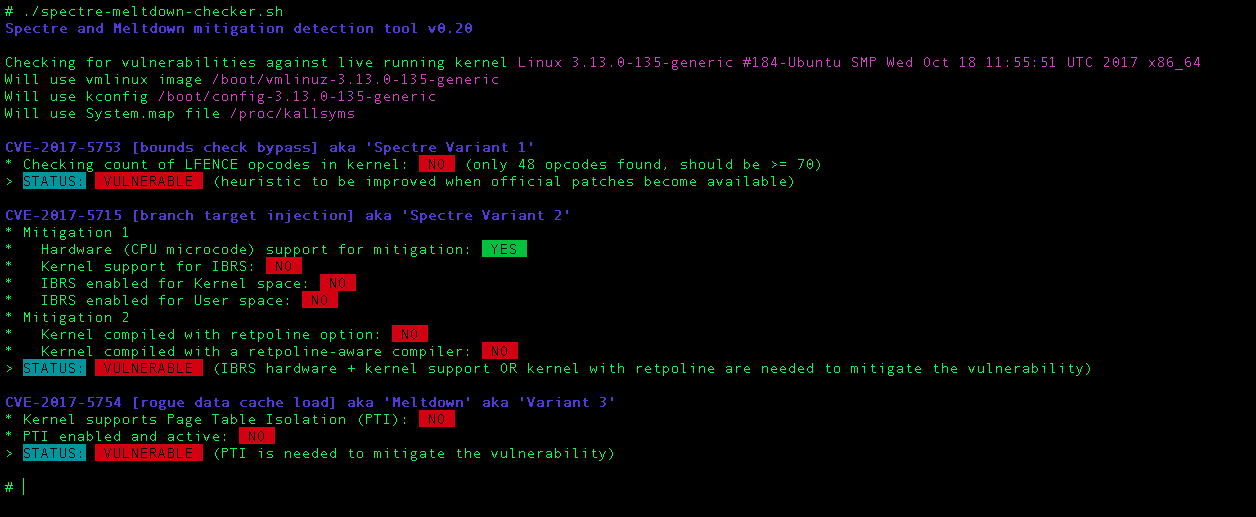
Executing the script will produce output similar to below,
It your server is vulnerable for all the 3 CVE’s, you’ll get output as above. You can consider safe if the STATUS is NOT VULNERABLE for all the 3CVE’s.
How to Address if my Linux server is vulnerable for Meltdown and Spectre ?
There is no permanent fix for this class of vulnerability unless there is a change in the CPU design. For now the only option is to update your kernel. You might probably need to keep updating over the next few weeks since there are lots of corner case bugs given that the testing involved here is complex.
The kernel/software updates provide workaround to mitigate the exploits by disabling or working around some of the optimized behaviour that leads to these vulnerabilities.
Different operating system providers have released patches to address Meltdown. While updates are also being released for Spectre, it represents an entire class of vulnerabilities, so it will likely require more extensive ongoing remediation.
Since the workaround is done by disabling the optimization routine, there will be possible degrade in the performance of the server. The extent of the slowdown is highly dependent on the type of work being performed, with I/O intensive processes experiencing the largest impact.
As of writing this article, Linux distributions have started to distribute patches, but no distributions are yet fully patched. Distributions that have released kernel updates with partial mitigation include:
Distributions that have released kernel updates with partial mitigation include:
- Ubuntu 17.10: kernel 4.13.0-25-generic
- Ubuntu 16.04: kernel 4.4.0-109-generic
- Ubuntu 14.04: kernel 3.13.0-139-generic
- CentOS 7: kernel 3.10.0-693.11.6
- CentOS 6: kernel 2.6.32-696.18.7
- Fedora 27: kernel 4.14.11-300
- Fedora 26: kernel 4.14.11-200
- Fedora 27 Atomic: kernel 4.14.11-300.fc27.x86_64
- Debian 9: kernel 4.9.0-5-amd64
- Debian 8: kernel 3.16.0-5-amd64
- Debian 7: kernel 3.2.0-5-amd64
- CoreOS: kernel 4.14.11-coreos
Steps to Apply the Update
Before upgrading kernel, note down the present kernel version
# uname -r
3.13.0-139-generic
Method to update Ubuntu/Debian:
Run the below command to update only the kernel.
# sudo apt-get update && sudo apt-get install linux-generic
Reboot the server,
# sudo shutdown -r 0
Verify your kernal version now,
# uname -r
Method to update CentOs/RedHat/Fedora:
# sudo yum update
Run the following command if you are using Fedora,
# sudo dnf update
Reboot the server,
# sudo reboot
Verify your kernal version now,
# uname -r
Public Cloud Providers Statement
AWS Processor Speculative Execution Research Disclosure
Below is an excerpt from AWS’ statement regarding this vulnerability
Concerning: CVE-2017-5715, CVE-2017-5753, CVE-2017-5754
Update As Of: 2018/01/08 14:25 PST
This is an update for this issue.
Amazon EC2
All instances across the Amazon EC2 fleet are protected from all known threat vectors from the CVEs previously listed. Customers’ instances are protected against these threats from other instances. We have not observed meaningful performance impact for the overwhelming majority of EC2 workloads.
Recommended Customer Actions for AWS Batch, Amazon EC2, Amazon Elastic Beanstalk, Amazon Elastic Container Service, Amazon Elastic MapReduce, and Amazon Lightsail
While all customer instances are protected, we recommend that customers patch their instance operating systems. This will strengthen the protections that these operating systems provide to isolate software running within the same instance. For more details, refer to specific vendor guidance on patch availability and deployment.
Google Cloud’s Security Bulletin
An excerpt from Google Security Bulletin
The infrastructure that runs Compute Engine and isolates customer VM instances from each other is protected against known attacks. Our mitigations prevent unauthorized access to our host systems from applications running inside VM instances. These mitigations also prevent unauthorized access between VM instances running on the same host system.
To prevent unauthorized access within your virtual machine instances, you must update the guest operating systems on those instances using one of the following options:
- Use patched public images to recreate your existing VM instances.
- On your existing instances, install patches provided by the operating system vendor for your distribution and reboot the patched instances.