- Openldap Tutorial – Practical Realtime Implementation and Integration
- Installation and configuration of openldap in Ubuntu
- Installing phpLDAPadmin – Web based LDAP Client
- Planning of LDAP DIT Structure and Config of Overlays ( access, ppolicy )
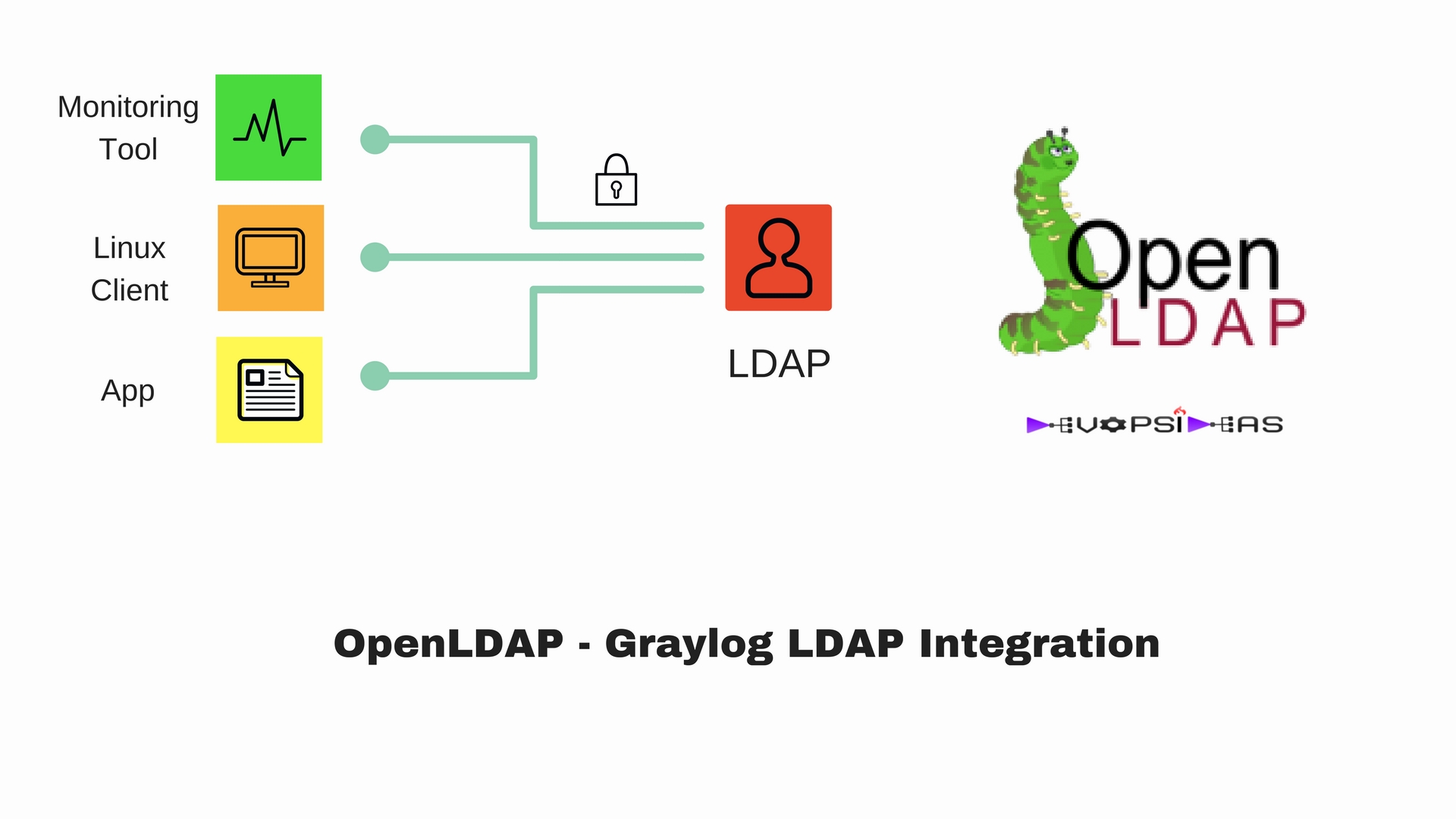
- OpenLDAP – Graylog LDAP Integration
- openLDAP – Linux Client LDAP Integration
- openLDAP – Basic Authentication using LDAP
- openLDAP – Self Service Password and Adhoc LDAP utilities
In this section we will cover Graylog LDAP Integration. We have enabled the necessary modules & overlays that are required for this integration in the previous section of this series. Now that we have the configurations ready, we need to start adding the entries as per the structure planned in the previous post.
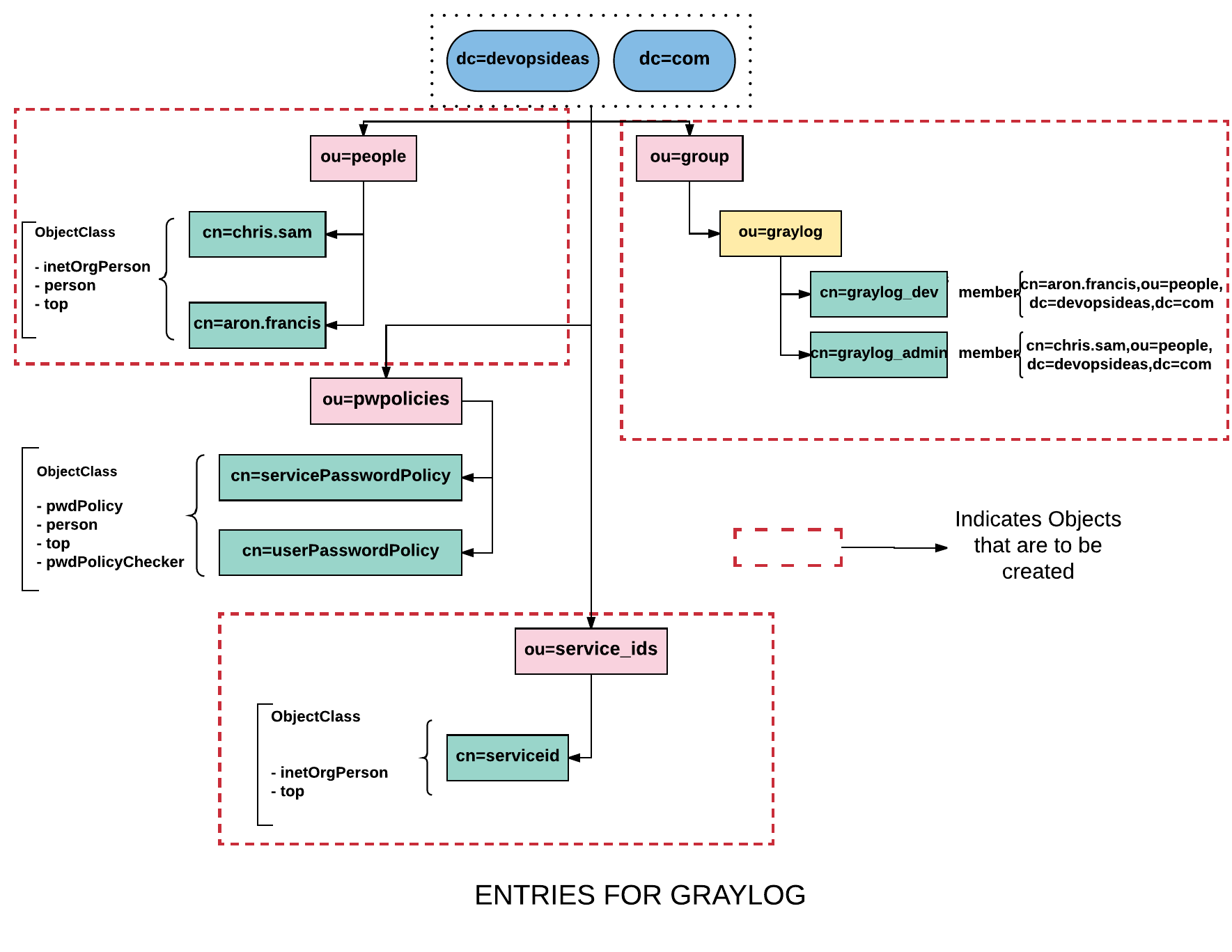
Add Entries
We need to create the entries depicted in the diagram. Since we already saw how to make changes using LDIF files and ldap commands, let’s do this using phpldapadmin this time.
Login to your phpldapadmin dashboard using http://<hostname>/phpldapadmin. You can refer this article to know more about phpldapadmin.
Once logged in, in the left hand side, you can see the Directory structure with entries. You’ll see a container for password policy (ou=pwpolicies) with entries in it created already. We created this entry while enabling ppolicy overlay in the previous article.
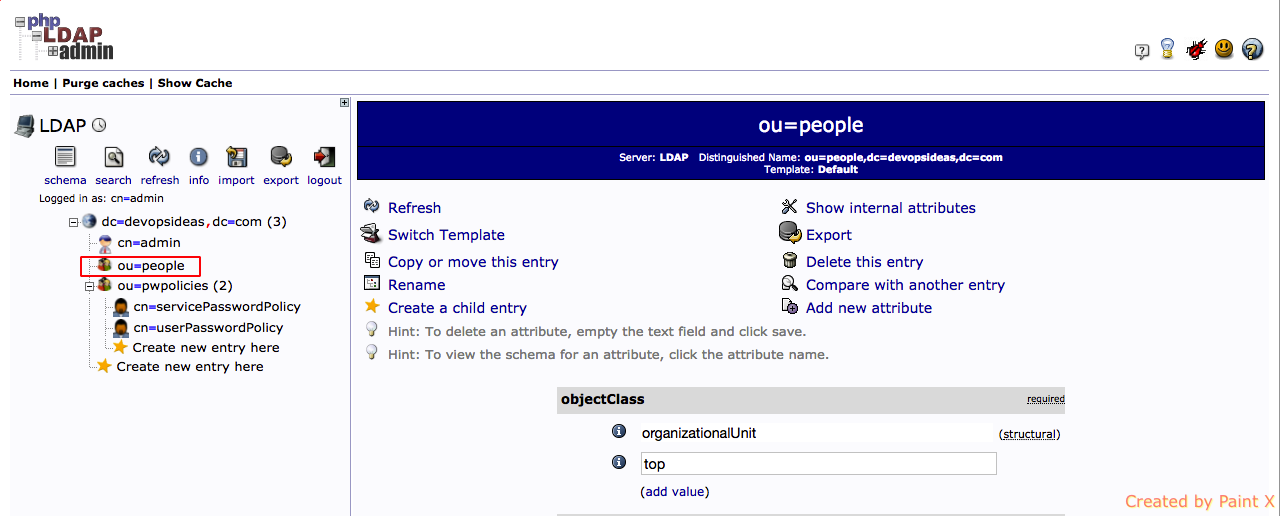
Create containers ( ou=people,ou=group )
First let us create a container for People (ou=people).
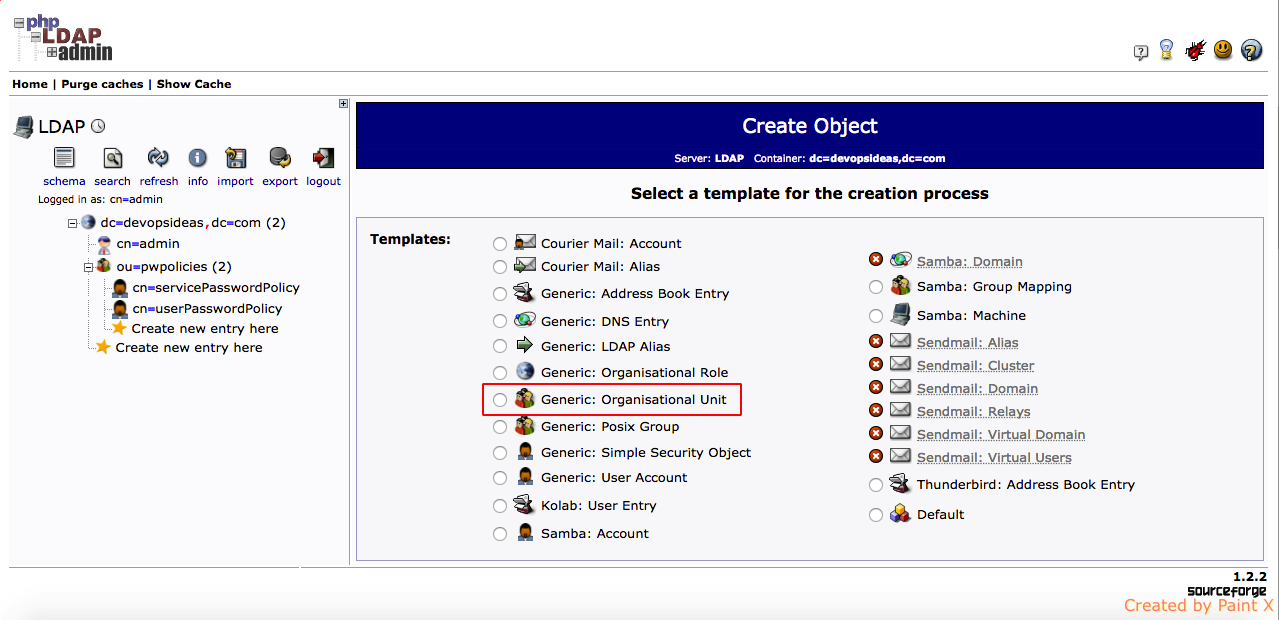
1) Click ‘Create new entry here‘ link available directly below the suffix ( dc=devopsideas,dc=com ) to add an entry.
2) Next, select ‘Oraganization Unit‘ for template (objectClass).
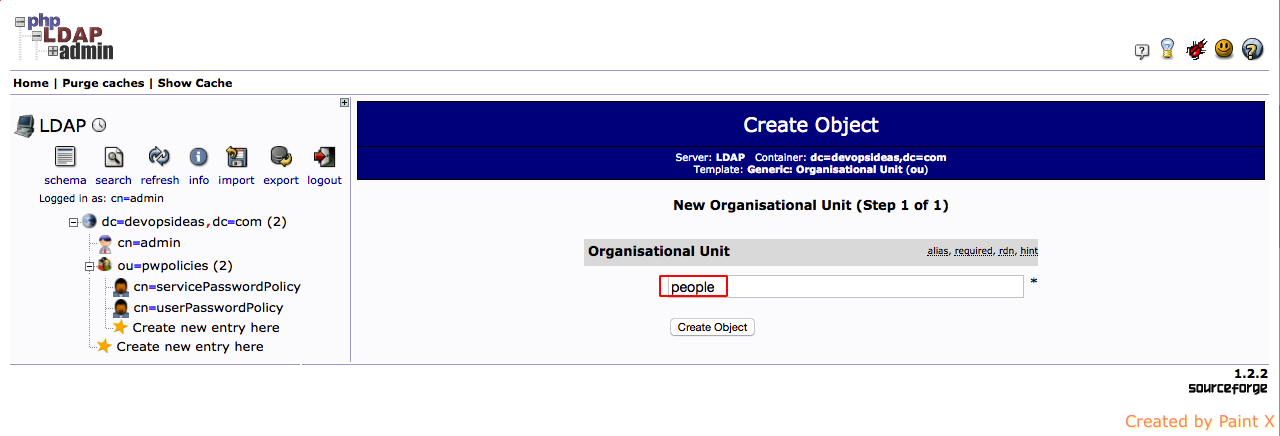
3) Give a name for the container (people in this case) and click ‘Create Object’,
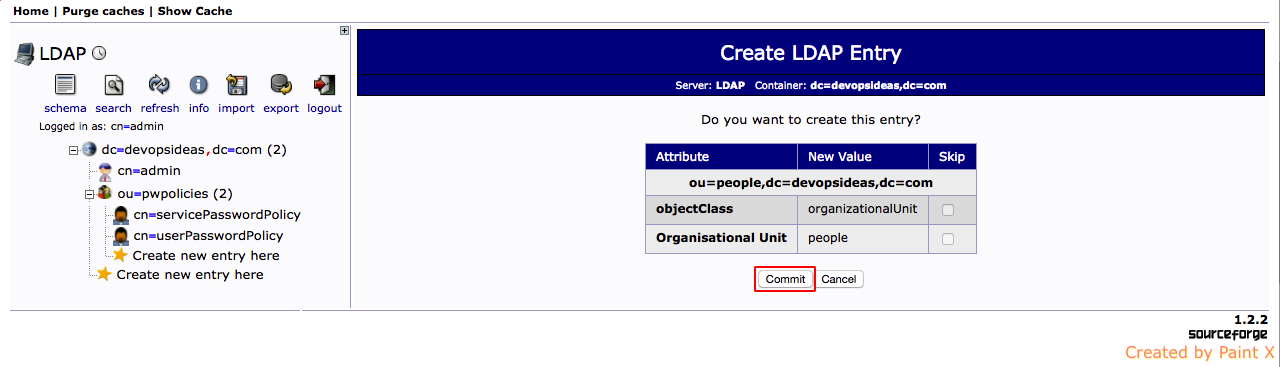
4) Click ‘commit’ button
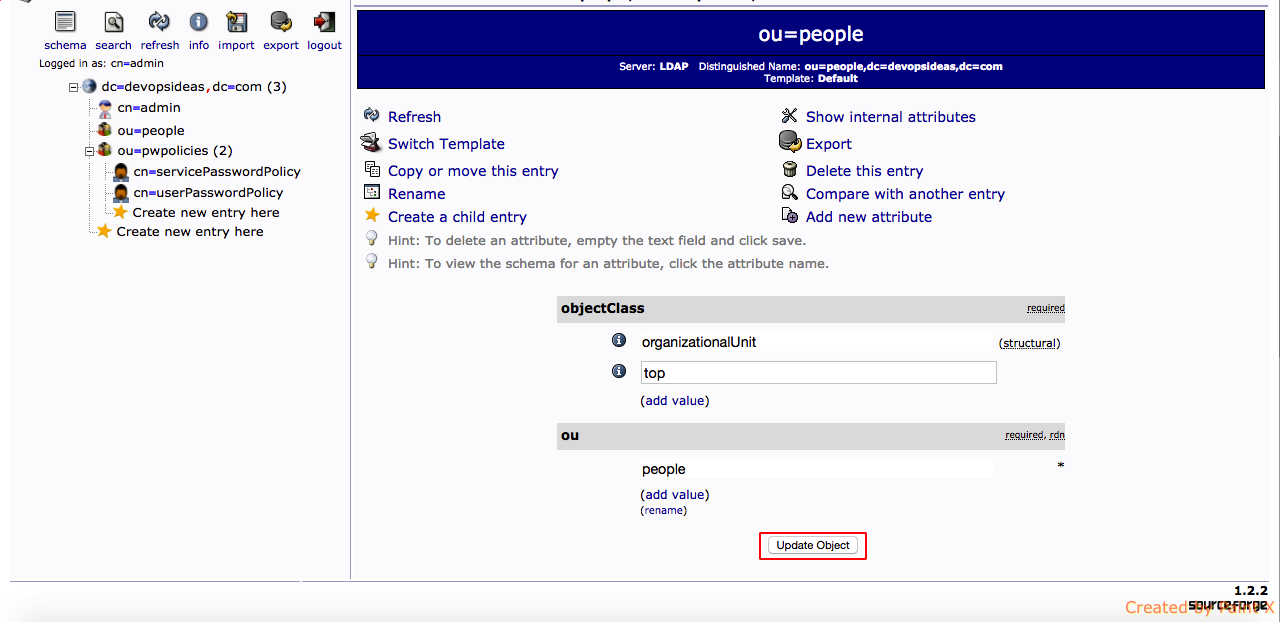
5) Click ‘Update’ to make the changes.
You’ll see the OU getting created. Follow the same steps and create the other container ‘ou=group’
Repeat the above steps for creating the second container ou=group
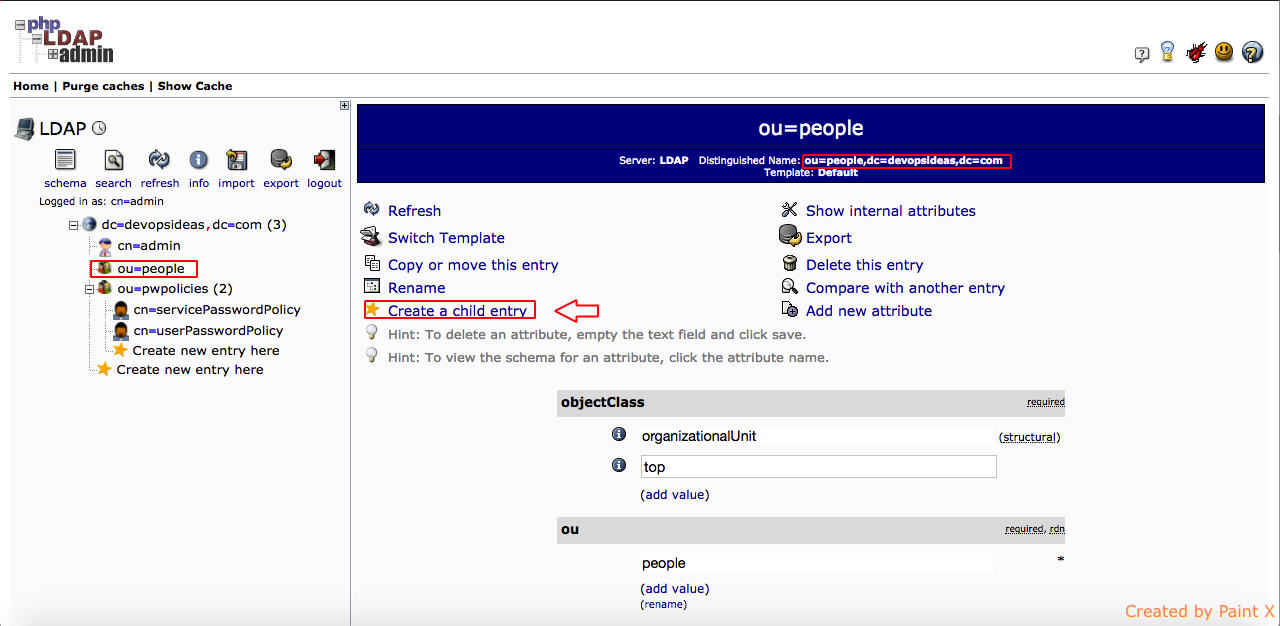
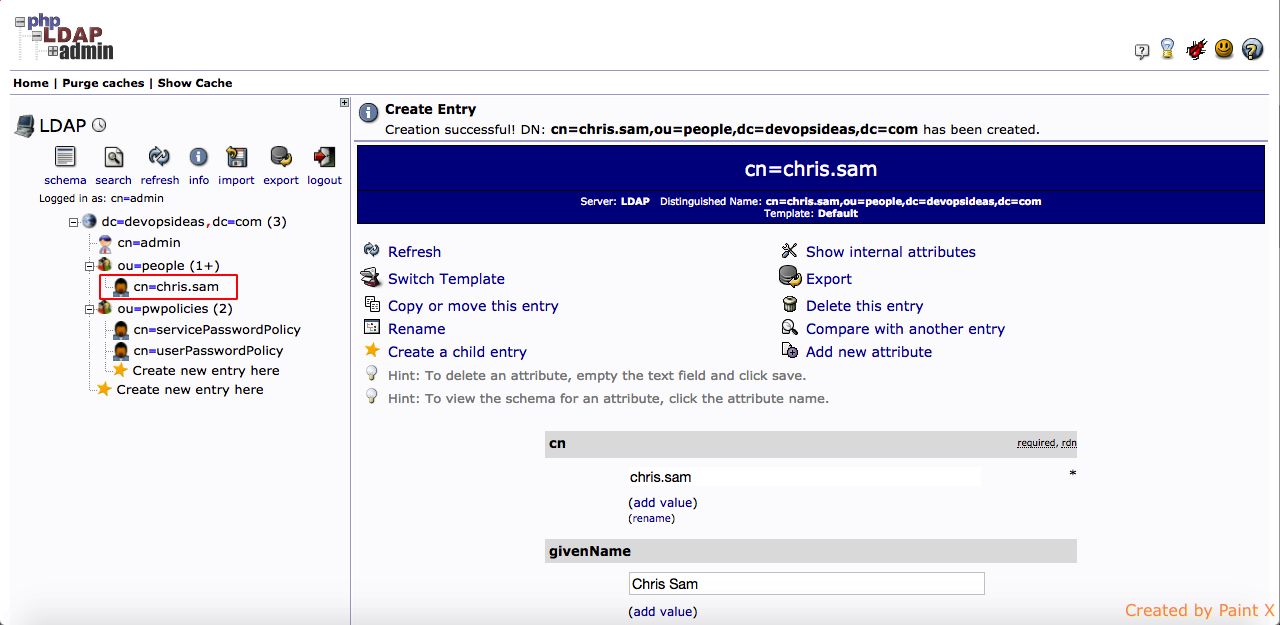
Create user entries for ou=people node
Next we need to add entries to the container created above. We’ll be adding two user’s, chris.sam and aron.francis
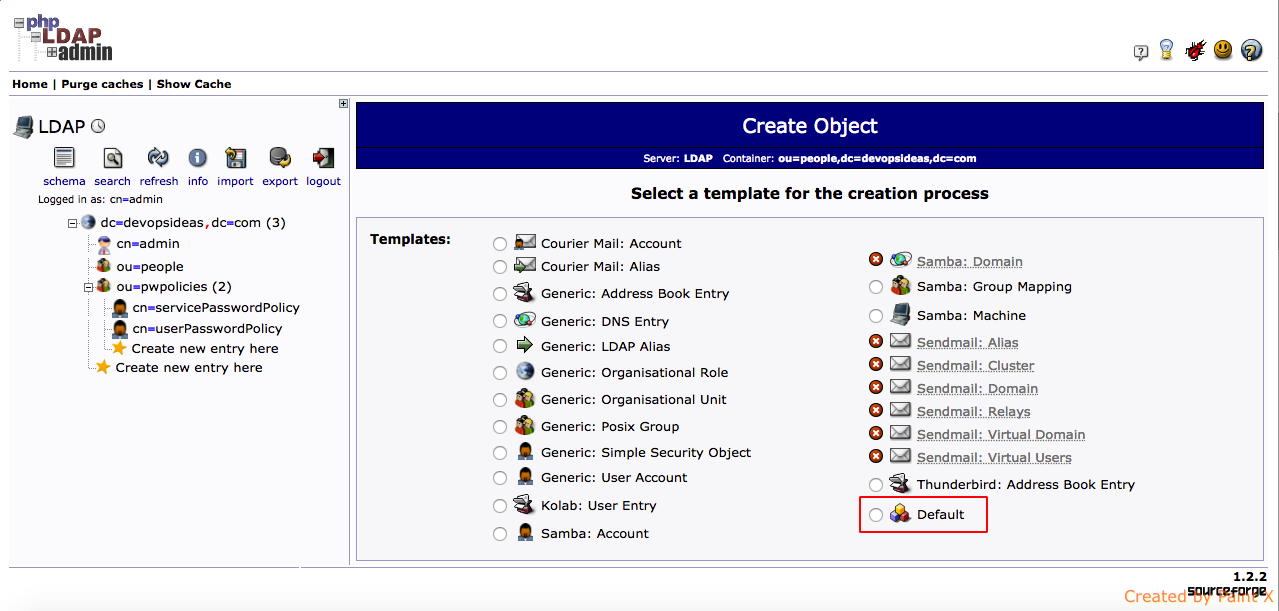
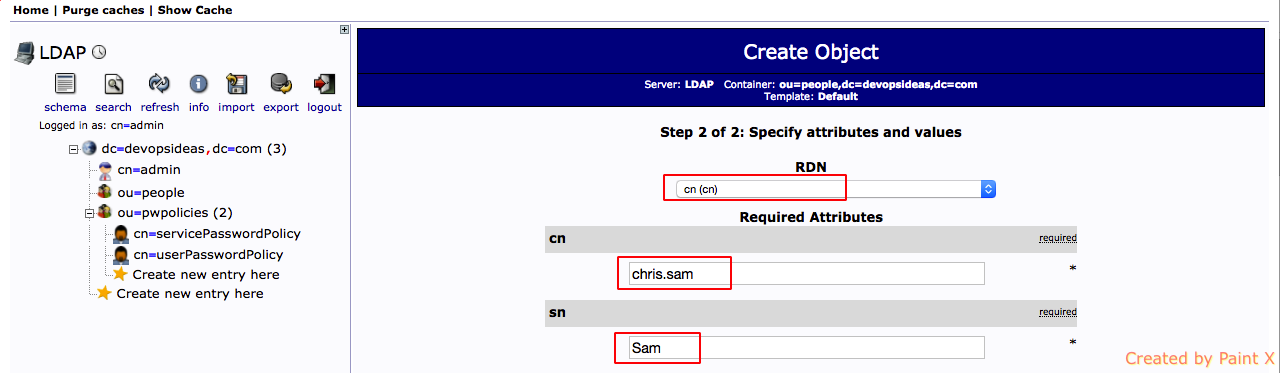
1) Click the container ou=people and select ‘Create a child entry’. Make sure you are under the right DN
2) Select default in the template section
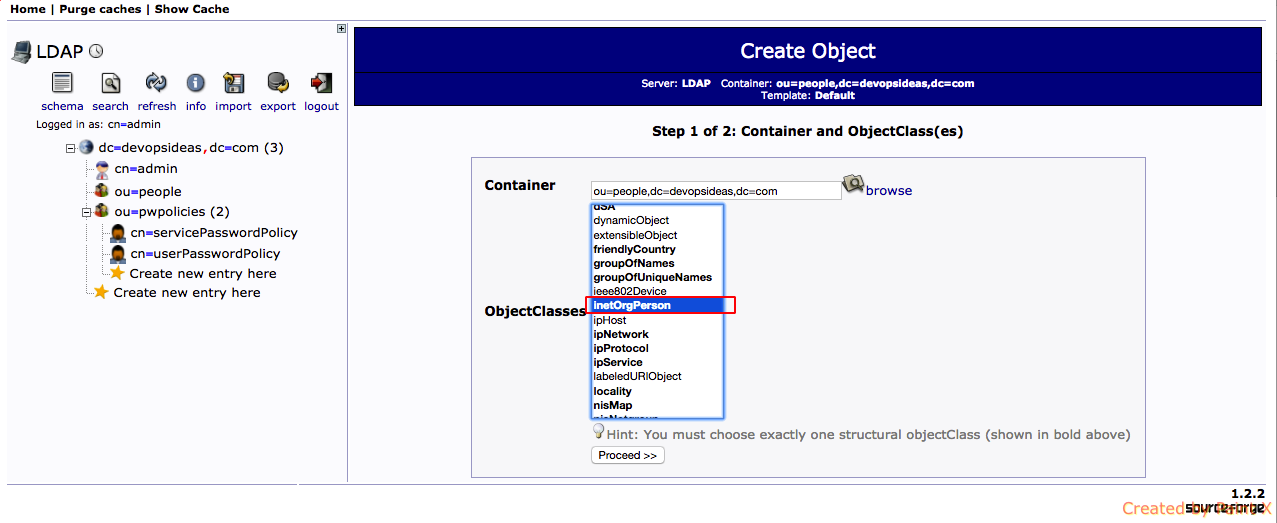
3) Select ineOrgPerson for objectClass and click Proceed.
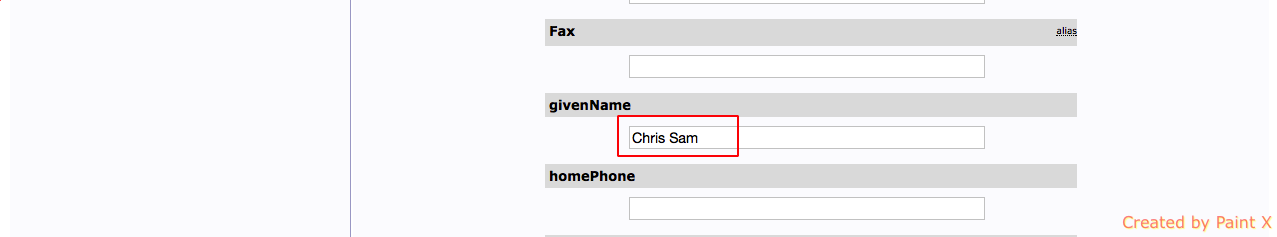
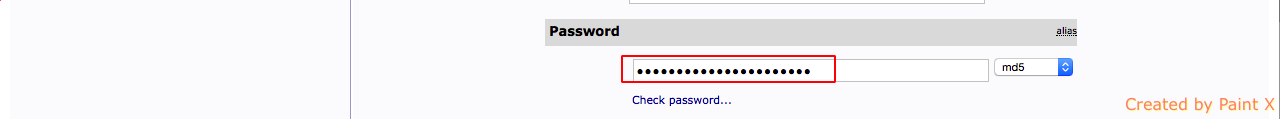
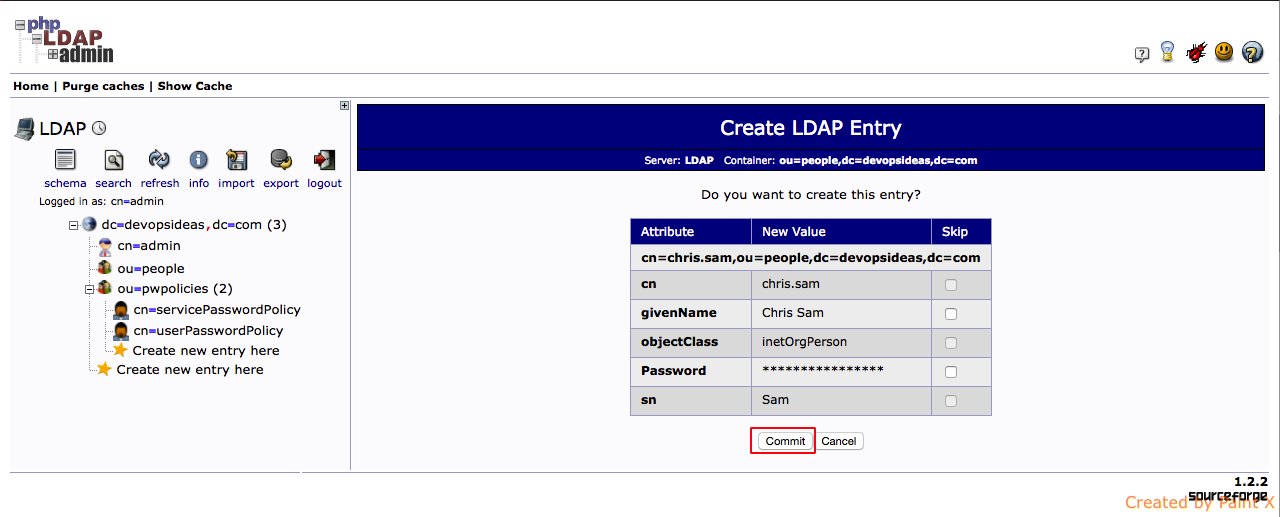
4) Select cn for RDN and enter values for cn, sn, givenName, password and click ‘Create Object’
5) You’ll be asked for confirm, click ‘commit’
6) You can find the object getting created under ou=people,dc=devopsideas,dc=com DN.
Repeat the above steps for creating the other user.
Create groups for Graylog
We still need to create an entity for graylog within ou=group,dc=devopsideas,dc=com and two entries representing graylog groups. We will be creating two entries for graylog group, graylog_dev and graylog_admin.
This time we will do this using LDIF file.
We will first create sub-container ou=graylog within the container ou=group,dc=devopsideas,dc=com. Create a file called subou.ldif and copy the below content
dn: ou=graylog,ou=group,dc=devopsideas,dc=com objectClass: organizationalUnit ou: graylog description: Graylog groups
Implement the change by running the below command,
ldapadd -W -Z -D cn=admin,dc=devopsideas,dc=com -f subou.ldif
Next, we will create the group for graylogs. Create a file named graylog_group.ldif and copy the below content.
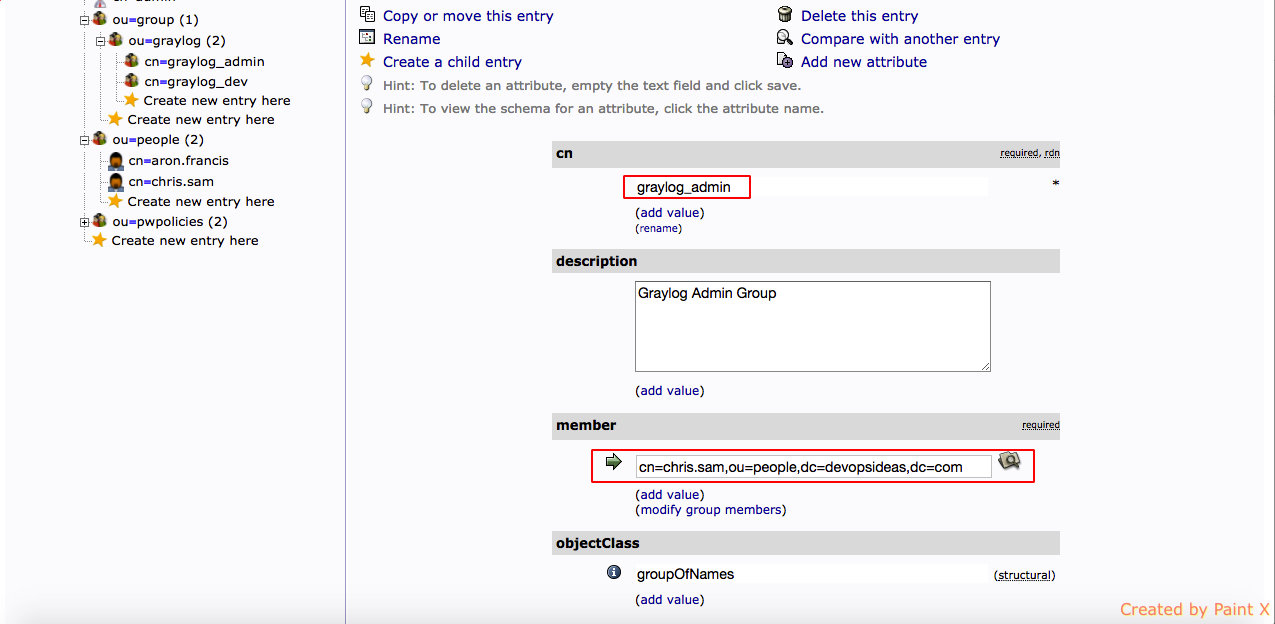
dn: cn=graylog_admin,ou=graylog,ou=group,dc=devopsideas,dc=com objectclass: groupOfNames cn: graylog_admin description: Graylog Admin Group member: cn=chris.sam,ou=people,dc=devopsideas,dc=com dn: cn=graylog_dev,ou=graylog,ou=group,dc=devopsideas,dc=com objectclass: groupOfNames cn: graylog_dev description: Graylog Dev Group member: cn=aron.francis,ou=people,dc=devopsideas,dc=com
Note that the objectClass we used here is groupOfNames. This objectClass is used for entries that represent a group that will hold members. As part of creating this entry we are adding members to it. chris.sam is added as part of graylog_admin and aron.francis is added as part of graylog_dev group.
Important: The memberOf is a dynamic attribute meaning that we need to manually load the module to use it. Every group created before this module is enabled has to be deleted and remade in order for these changes to take effect. Refer this article to know more about memberOf overlay and how to enable it.
Implement this change by running the below command,
ldapadd -W -Z -D cn=admin,dc=devopsideas,dc=com -f graylog_group.ldif
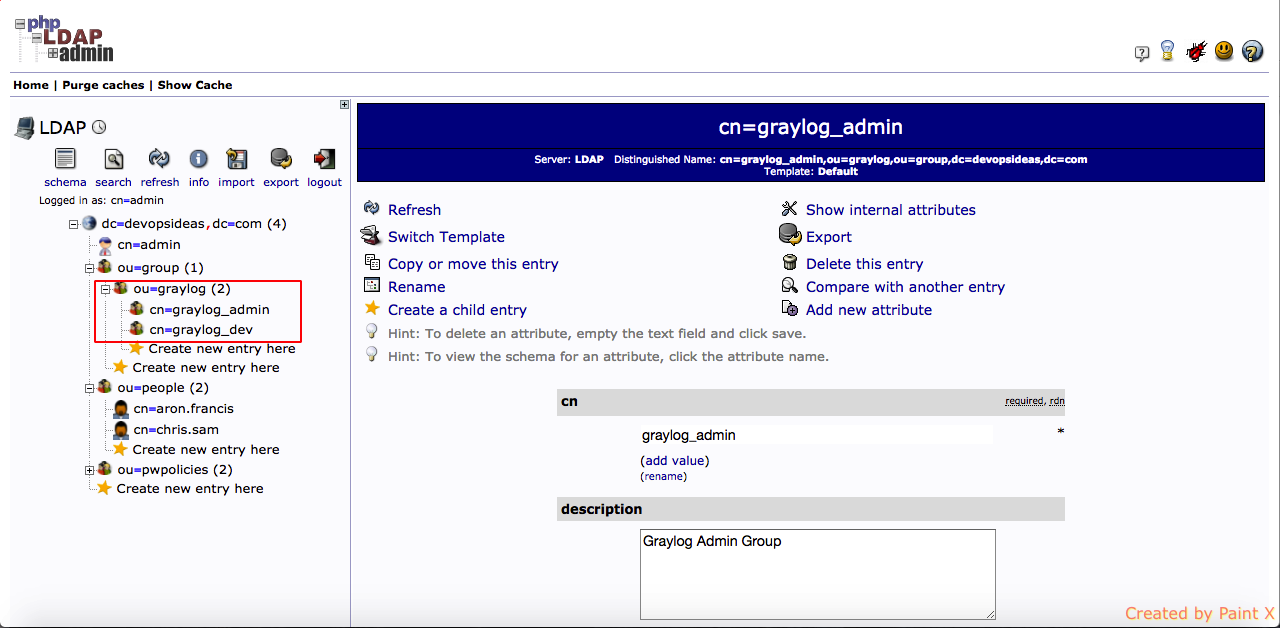
Let us verify if the changes are made by viewing phpldapadmin.
You’ll see the graylog group getting created as shown below.
You’ll also see users in the member attribute.
Create serviceid for Graylog
Similar to the user entry, create a service id for binding graylog under ou=service_ids node. We are yet to create the service_ids container. Create a file named serviceou.ldif with the below content
dn: ou=service_ids,dc=devopsideas,dc=com objectClass: organizationalUnit ou: service_ids description: Group for Service ids
Run the below command to create the container,
ldapadd -W -Z -D cn=admin,dc=devopsideas,dc=com -f serviceou.ldif
Create a file named serviceid.ldif with the below content
dn: cn=serviceid,ou=service_ids,dc=devopsideas,dc=com
cn: serviceid
givenName: Service ID
sn: id
uid: serviceid
objectClass: top
objectClass: inetOrgPerson
objectClass: person
userPassword: {SHA}qUqP5cyxm6YcTAhz05Hph5gvu9M=
The password hash can be created as below,
$ slappasswd -h {SHA} -s <password>
{SHA}qUqP5cyxm6YcTAhz05Hph5gvu9M=
Make a note of this password since we will use in LDAP configuration in Graylog.
Create the serviceid entry by running the below command,
ldapadd -W -Z -D cn=admin,dc=devopsideas,dc=com -f serviceid.ldif
If you recollect, we have set a separate password policy for service id’s and we need to apply that for this id. Create a file named serviceid_ppolicy.ldif with the below content.
dn: cn=serviceid,ou=service_ids,dc=devopsideas,dc=com changetype: modify add: pwdPolicySubentry pwdPolicySubentry: cn=servicePasswordPolicy,ou=pwpolicies,dc=devopsideas,dc=com
Run the below command,
ldapmodify -W -Z -D cn=admin,dc=devopsideas,dc=com -f serviceid_ppolicy.ldif
The serviceid DN will now have ‘cn=servicePasswordPolicy,ou=pwpolicies,dc=devopsideas,dc=com’ as its password policy definition.
We have everything in place now for integrating Graylog with LDAP. Let’s do it
Graylog LDAP Integration
This article explains just the integration of Graylog with LDAP. Installation and configuration of graylog is beyond the scope of this article. Please refer Centralized logging using Graylog for more on that.
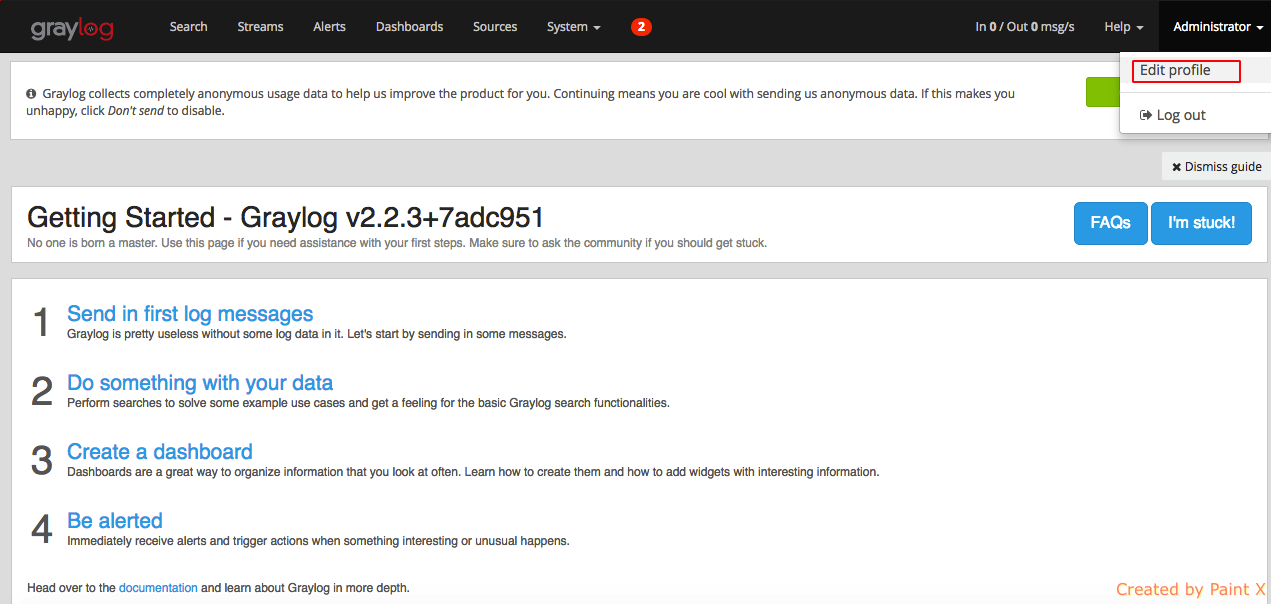
1) Login into Graylog Dashboard as admin and click Administrator–>Edit Profile
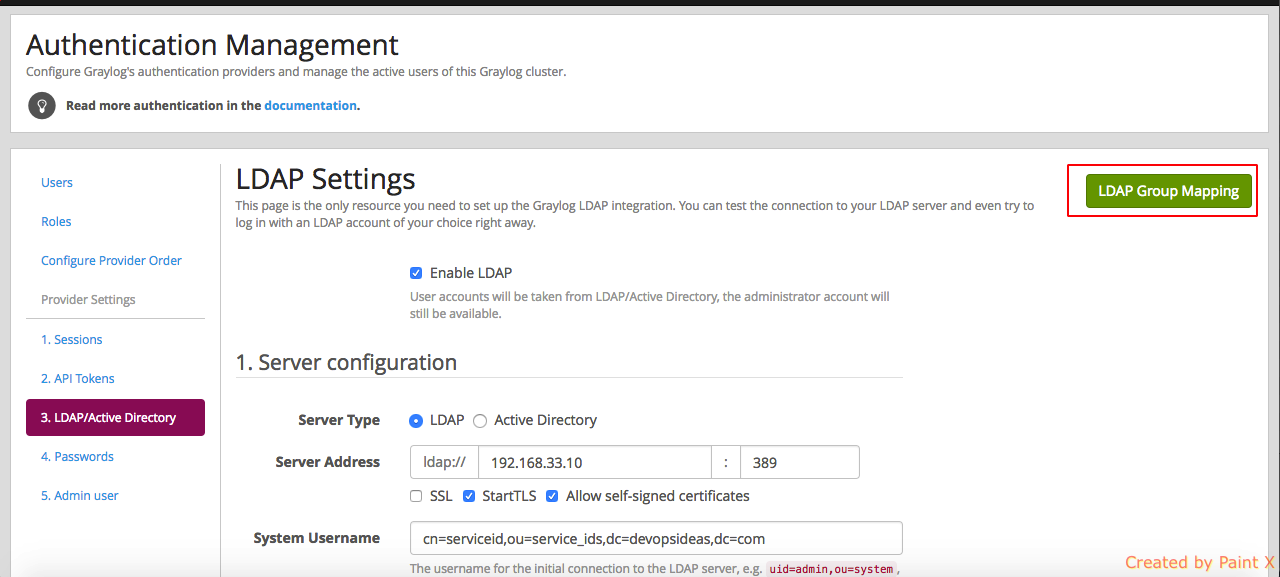
2) Select LDAP / Active Directory
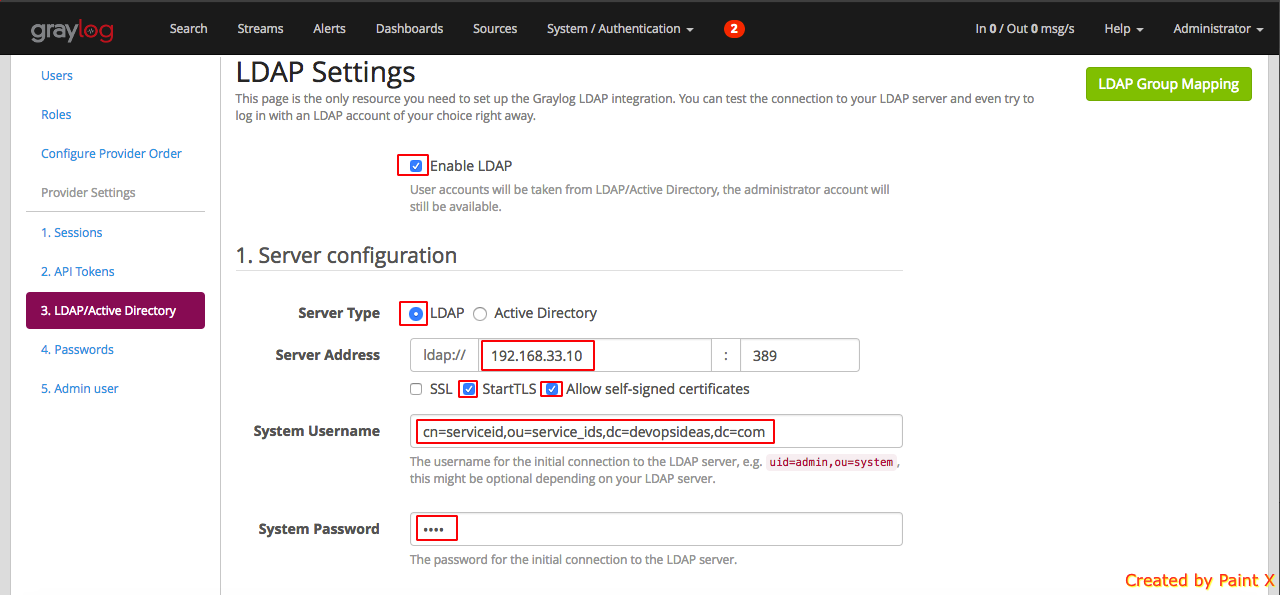
3) Enable the ‘Enable LDAP’ checkbox. In the Server Configuraiton, pass in the IP or Domain Name of your LDAP host. Enable StartTLS and Allow self-signed certificates. In ‘System Username’ pass in the service id (cn=serviceid,ou=service_ids,dc=devopsideas,dc=com) which we created earlier for binding. System Password should be the password of servicd id.
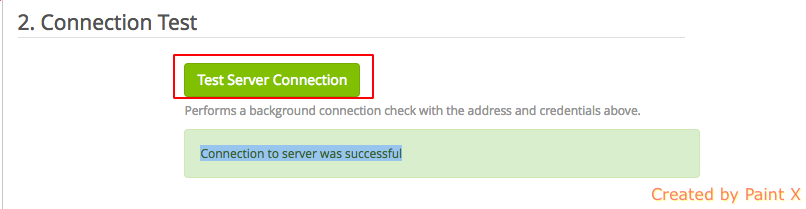
4) Test Server Connection. If everything goes fine, you’ll get ‘Connection to server was successful’
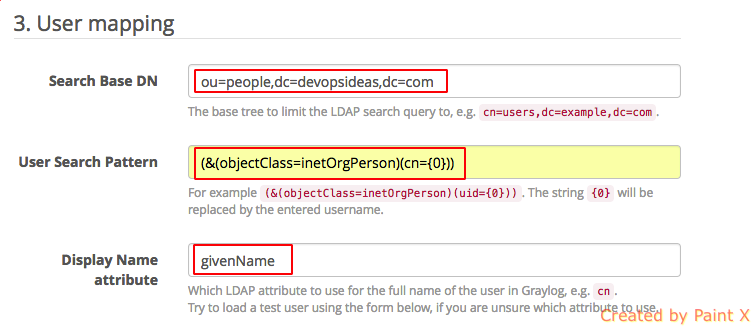
5) In User mapping,
Search Base DN : ou=people,dc=devopsideas,dc=com. This indicates where the search will start from.
User Search Pattern: (&(objectClass=inetOrgPerson)(cn={0})). This search will filter for entry having objectClass as inetOrgPerson and id passed in the login page
Display Name attribute: givenName. This will be used for displaying the user name in the top right corner of the dashboard
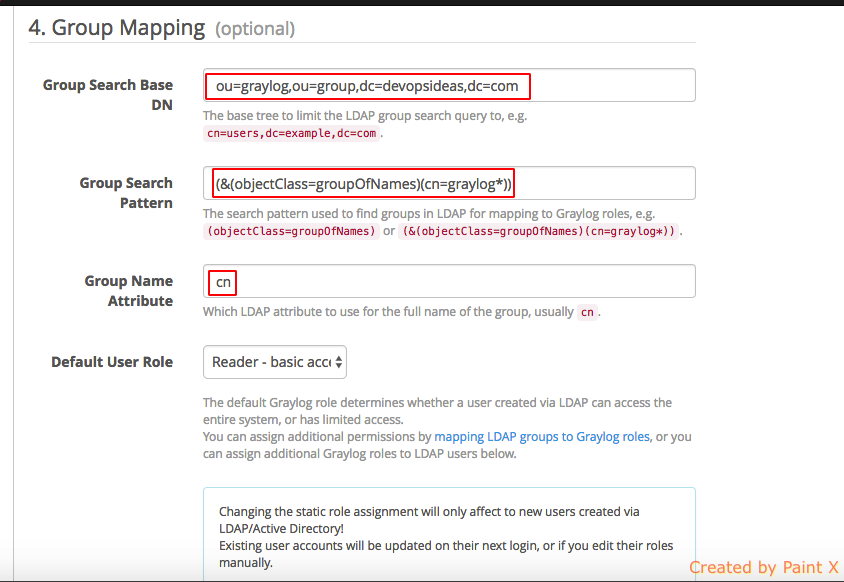
6) In group mapping, we will be using filters to retrieve the group and map it with graylog roles.
Group Search Base DN: ou=graylog,ou=group,dc=devopsideas,dc=com. This denotes from where the search will start.
Group Search Pattern: (&(objectClass=groupOfNames)(cn=graylog*)). This pattern uses the AND condition to retrieve the entries that has a groupOfNames as objectClass and the cn’s that starts with graylog. So this will retrieve both the groups we created ( graylog_admin & graylog_dev )
Group Name Attribute: cn . This will be the attribute used for mapping the LDAP group with Graylog roles.
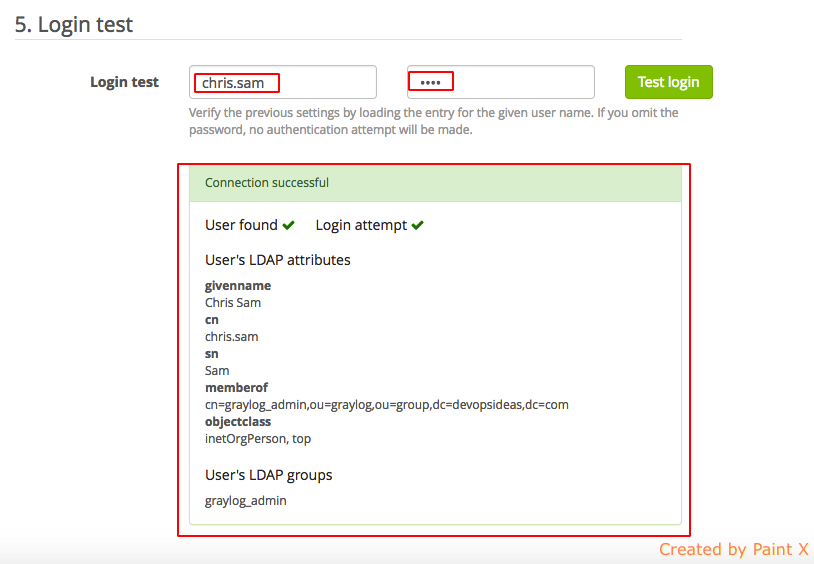
7) Login Test
Test your configuration by passing in username and password of an LDAP user. Your connection will succeed if your configuration is flawless. You’ll see all the details related to the user.
8) Save the LDAP configuration
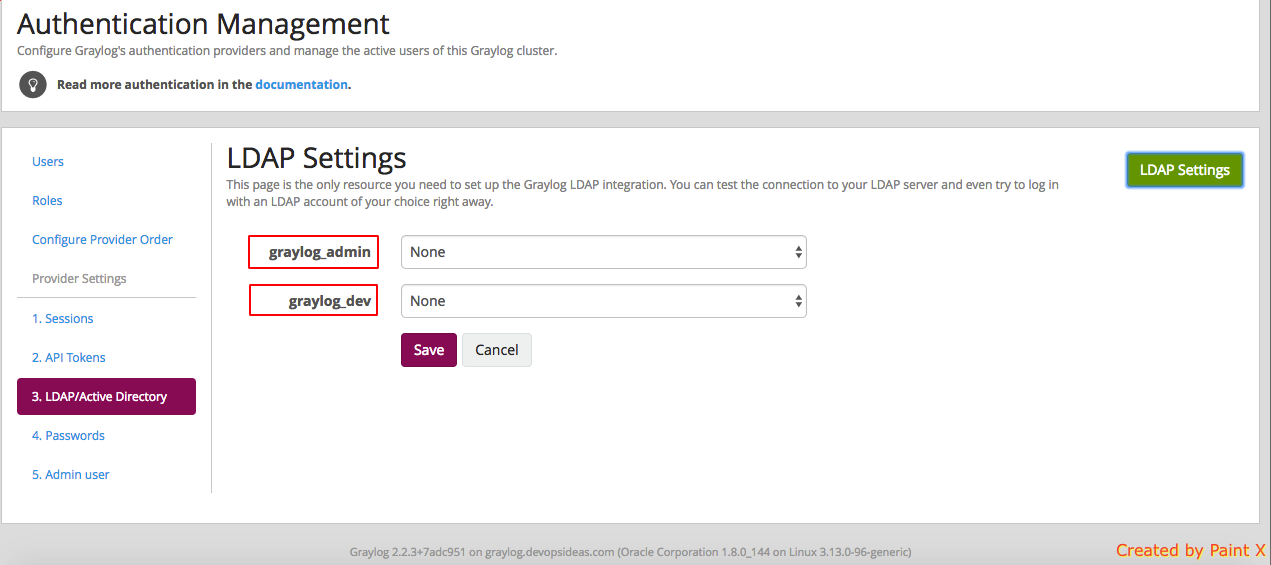
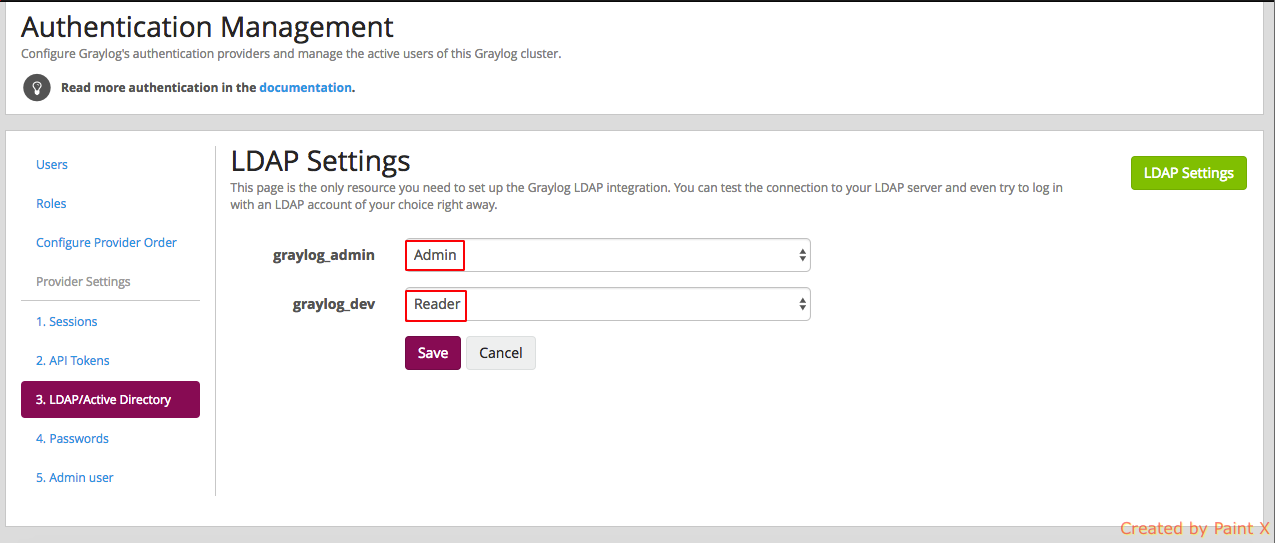
9) In the same page, click ‘LDAP Group Mappings’
10) You’ll see graylog retrieving the group names we specified in LDAP.
11) Map the roles with the corresponding group. In this case we will map graylog_admin to Admin role and graylog_dev to Reader rolea and click save.
Verification:
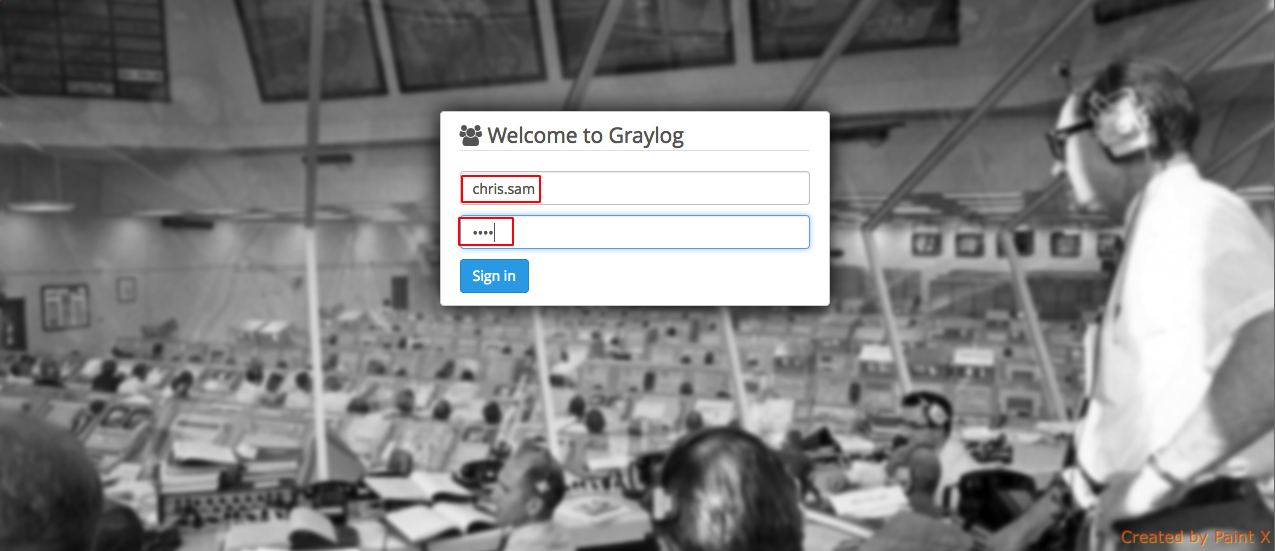
We have completed Integrating graylog with LDAP for authentication. You can verify it by logging in as one of the LDAP user who’s part of the graylog group.
We’ll
test the admin user chris.sam
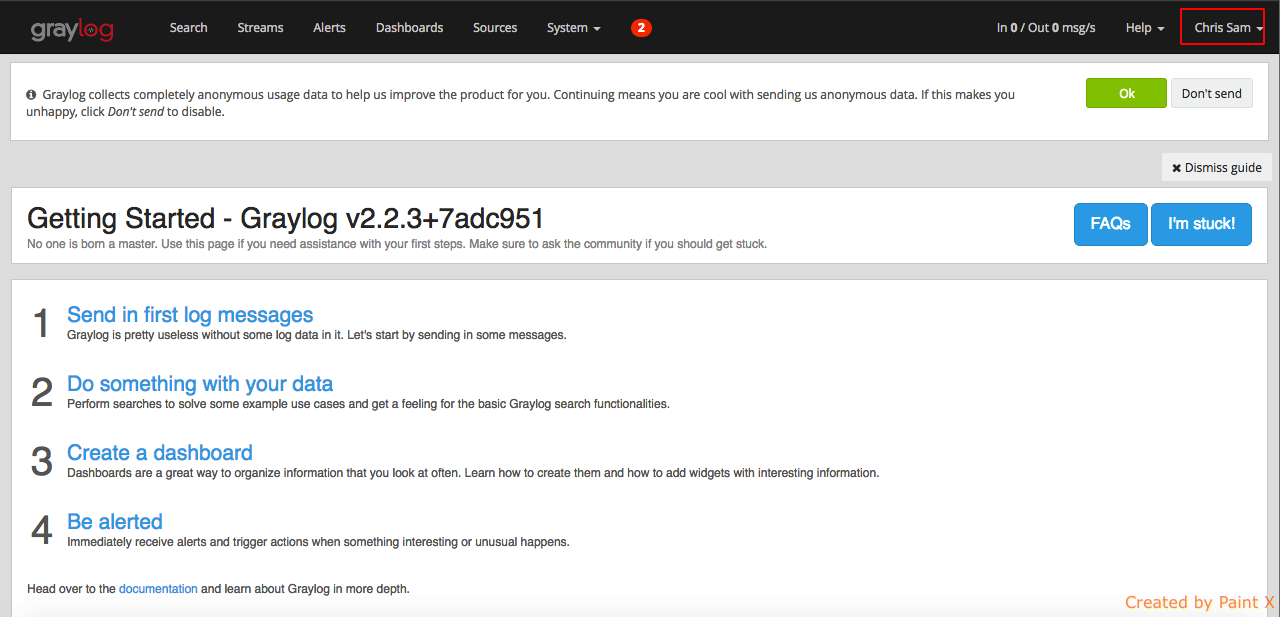
Once logged in, you’ll see the full user name in the top right corner ( we got this using ‘givenName’ attribute ). This user will have admin access since he’s part of graylog_admin group.
You can repeat the steps to test the other user who only has ‘Reader’ access since he’s part of graylog_dev group.
We’ve successfully completed Graylog LDAP Integration. Up next we will see how we can connect Linux clients to LDAP for authentication.