- Openldap Tutorial – Practical Realtime Implementation and Integration
- Installation and configuration of openldap in Ubuntu
- Installing phpLDAPadmin – Web based LDAP Client
- Planning of LDAP DIT Structure and Config of Overlays ( access, ppolicy )
- OpenLDAP – Graylog LDAP Integration
- openLDAP – Linux Client LDAP Integration
- openLDAP – Basic Authentication using LDAP
- openLDAP – Self Service Password and Adhoc LDAP utilities
What we will do ?
Based on our scenario, we assume that some application has been protected using basic authentication configured in apache. We will implement Basic Authentication using LDAP and configure apache to use LDAP for authentication.
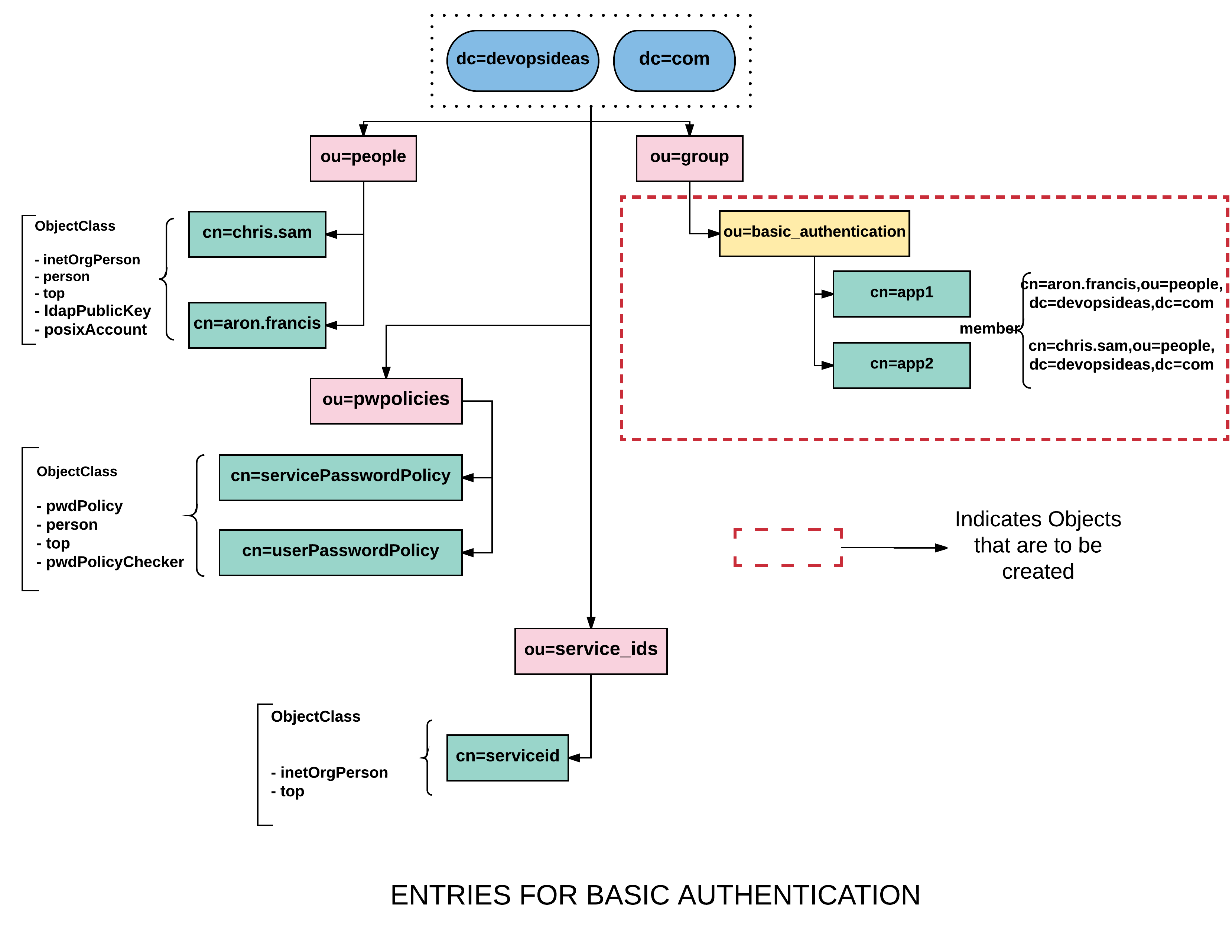
As we usually did in all our previous cases, we need to create a separate group for managing access to the application. Refer the below diagram to understand what needs to be created.
Create a container ( ou=basic_authentication )
Create a file named basicauthou.ldif with the below content,
dn: ou=basic_authentication,ou=group,dc=devopsideas,dc=com objectClass: organizationalUnit ou: server description: Group for managing application access
Run the below command to implement the change,
ldapadd -Z -W -D cn=admin,dc=devopsideas,dc=com -f basicauthou.ldif
Create app group entries for ou=basic_authentication
Create a file named basicauthgroup.ldif with the below content,
dn: cn=app1,ou=basic_authentication,ou=group,dc=devopsideas,dc=com objectclass: groupOfNames cn: app1 description: app1 Group member: cn=chris.sam,ou=people,dc=devopsideas,dc=com member: cn=aron.francis,ou=people,dc=devopsideas,dc=com dn: cn=app2,ou=basic_authentication,ou=group,dc=devopsideas,dc=com objectclass: groupOfNames cn: app2 description: app2 Group member: cn=chris.sam,ou=people,dc=devopsideas,dc=com member: cn=aron.francis,ou=people,dc=devopsideas,dc=com
Create the entries by running the below command,
ldapadd -Z -W -D cn=admin,dc=devopsideas,dc=com -f basicauthgroup.ldif
We have everything ready from LDAP server side. Up next we will configure apache basic authentication config to point to LDAP
Enable authnz_ldap module
As a first step in the server where apache runs, you need to enable the authnz_ldap module
a2enmod authnz_ldap
Restart apache server after enabling the module
systemctl restart apache2.service
Update cert path in apache ldap.conf
Since we have enforced TLS for connections at LDAP server, we need update apache ldap config to point to the TLS cacert. Copy the cacert.pem generated in this section to the server where apache is running.
Assuming, the cert is placed in ‘/etc/ldap/certs/cacert.pem’, we will update it in apache’s ldap.conf file
Open the file ‘/etc/apache2/mods-enabled/ldap.conf’ in vi and add the below content
LDAPTrustedGlobalCert CA_BASE64 /etc/ldap/certs/cacert.pem
Save the file and reload apache
systemctl reload apache2.service
Update Basic Auth to point to LDAP
Update the virtual host for which you have configured basic authentication. For example,
<VirtualHost *:80> ServerAdmin webmaster@localhost DocumentRoot /var/www/html <Directory /var/www/html/app1> AuthType Basic AuthName "app1 LDAP Auth" AuthBasicProvider ldap AuthLDAPURL "ldap://ldap.devopsideas.com:389/ou=people,dc=devopsideas,dc=com?uid" TLS AuthLDAPBindDN "cn=serverid,ou=service_ids,dc=devopsideas,dc=com" AuthLDAPBindPassword "<serverid_passwd>" Require ldap-group cn=app1,ou=basic_authentication,ou=group,dc=devopsideas,dc=com </Directory> <Directory /var/www/html/app2> AuthType Basic AuthName "app2 LDAP Auth" AuthBasicProvider ldap AuthLDAPURL "ldap://ldap.devopsideas.com:389/ou=people,dc=devopsideas,dc=com?uid" TLS AuthLDAPBindDN "cn=serverid,ou=service_ids,dc=devopsideas,dc=com" AuthLDAPBindPassword "<serverid_passwd>" Require ldap-group cn=app2,ou=basic_authentication,ou=group,dc=devopsideas,dc=com </Directory> ErrorLog ${APACHE_LOG_DIR}/error.log CustomLog ${APACHE_LOG_DIR}/access.log combined </VirtualHost>
AuthLDAPURL specifies the URI of the ldap server along with the search base. It also contains the attribute at the end (uid) that will be used for autheticating
AuthLDAPBindDN Denotes the bindDN that will be used. Here we are re-using the ‘serverid’ which we created earlier while Integrating Linux client.
Require ldap-group is more like the memberOf attribute that we use to filter user.
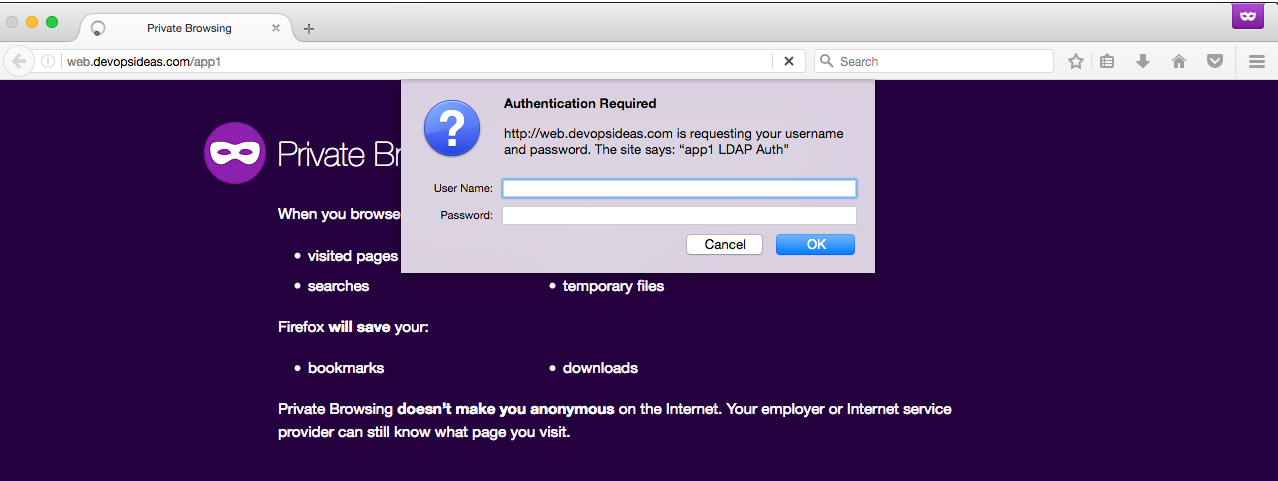
Restart apache after making the changes and access the application in the browser. Let’s access app1 and see if it works.
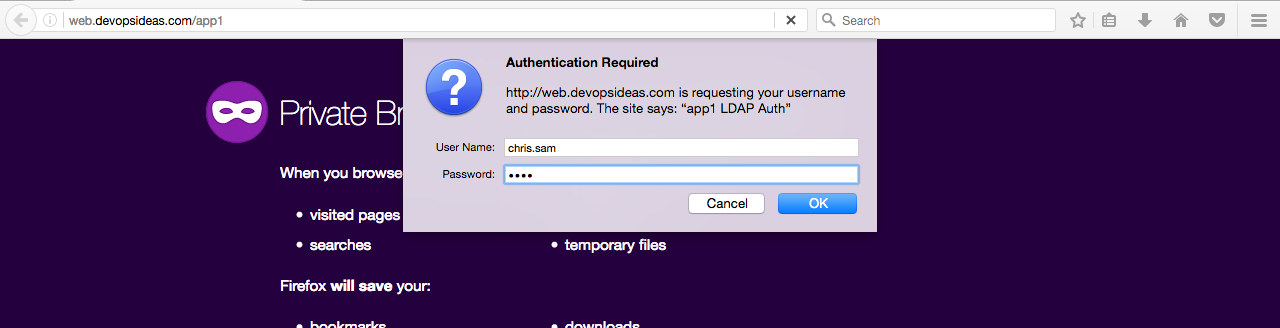
Pass in the credentials,
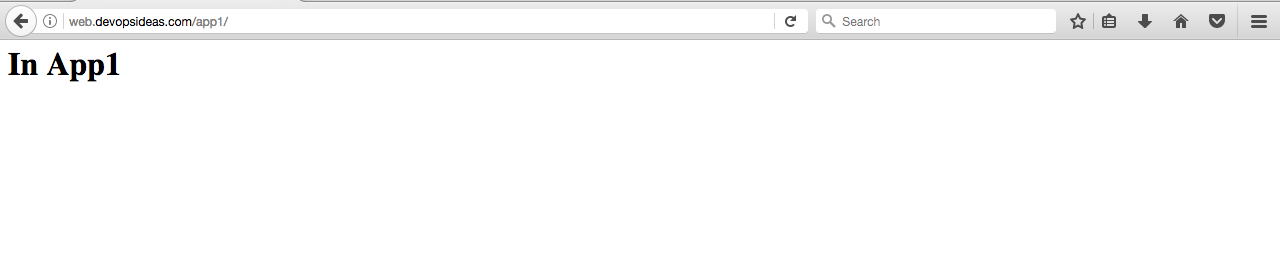
It works!!
That’s it!!. With this we have completed all the 3 cases as stated in the scenario. Up next we will see some Ad-hoc utilities that will help us managing openLDAP in a better way.